
Features:
VM Sandboxing
Complement your established defenses with cuttingedge capability — analyzing suspicious and high-risk files in a contained environment to uncover the full attack lifecycle using system activity and callback detection.
File Analysis Tools
Reports with captured packets, original file, tracer log and screenshot provide rich threat intelligence and actionable insight after files are examined. This is to speed up remediation and updated protection.
Remediation
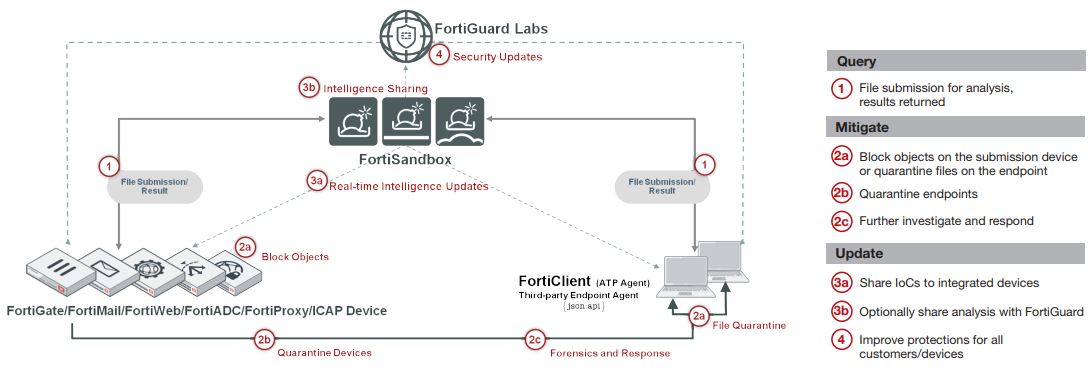
Fortinet's ability to uniquely integrate various products with FortiSandbox offers automatic protection with incredibly simple setup. Once a malicious code is determined, the analyzer will develop and forward the dynamically generated signature to all registered devices and clients. These devices then examine subsequent files against the latest DB.
 Multi-tiered file processing optimizes resource usage that improves security, capacity and performance
Multi-tiered file processing optimizes resource usage that improves security, capacity and performance
AV Engine
- Applies top-rated (95%+ Reactive and Proactive) AV Scanning. Serves as an efficient pre-filter.
Cloud Query
- Real-time check of latest malware information
- Access to shared information for instant malware detection
Code Emulation
- Quickly simulates intended activity
- OS independent and immune to evasion/obfuscation
Full Virtual Sandbox
- Secure run-time environment for behavioral analysis/rating
- Exposes full threat lifecycle information
Call Back Detection
- Identifies the ultimate aim, call back and exfiltration
Features Summary
Administration
- Supports WebUI and CLI configurations
- Multiple administrator account creation
- Configuration file backup and restore
- Notification email when malicious file is detected
- Weekly report to global email list and FortiGate administrators
- Centralized search page which allows administrators to build customized search conditions
- Frequent signature auto-updates
- Automatic check and download new VM images
- VM status monitoring
- Radius Authentication for administrators
Networking/Deployment
- Static Routing Support
- File Input: Offline/sniffer mode, On-demand file upload, file submission from integrated device(s)
- Option to create simulated network for scanned file to access in a closed network environment
- High-Availability Clustering support
- Port monitoring for fail-over in a cluster
Systems Integration
- File Submission input: FortiGate, FortiClient, FortiMail, FortiWeb
- File Status Feedback and Report: FortiGate, FortiClient, FortiMail, FortiWeb
- Dynamic Threat DB update: FortiGate, FortiClient, FortiMail
- Periodically push dynamic DB to registered entities.
- File checksum and malicious URL DB
- Update Database proxy: FortiManager
- Remote Logging: FortiAnalyzer, syslog server
- Web-based API with which users can upload samples to scan indirectly
- Bit9 end point software integration
Advanced Threat Protection
- Virtual OS Sandbox:
- Concurrent instances
- OS type supported: Windows XP, Windows 7, Windows 8.1, Windows 10 and Android
- Anti-evasion techniques: sleep calls, process and registry queries
- Callback Detection: malicious URL visit, Botnet C&C communication and attacker traffic from activated malware
- Download Capture packets, Original File, Tracer log and Screenshot
- File type support:
- Archived: .tar, .gz, .tar.gz, .tgz, .zip, .bz2, .tar.bz2, .bz, .tar.Z,.cab, .rar, .arj
- Executable files: (eg: .exe, .dll), PDF, Windows Office Document, AdobeFlash and JavaArchive (JAR) files
- Script files: .js,.bat,.vbs,.ps1,.cmd
- Media files: .avi, .mpeg, .mp3, .mp4
- Protocols/applications supported:
- Sniffer mode: HTTP, FTP, POP3, IMAP, SMTP, SMB
- Integrated mode with FortiGate: HTTP, SMTP, POP3, IMAP, MAPI, FTP, IM and their equivalent SSL encrypted versions
- Integrated mode with FortiMail: SMTP, POP3, IMAP
- Integrated mode with FortiWeb: HTTP
- Customize VMs with support file types support
- Isolate VM image traffic from system traffic
- Network threat detection in Sniffer Mode: Identify Botnet activities and network attacks, malicious URL visit
- Scan SMB/NFS network share and quarantine suspicious files. Scan can be scheduled
- Scan embedded URLs inside document files
- Integrate option for third partyYara rules
- Option to auto-submit suspicious files to cloud service for manual analysis and signature creation
- Option to forward files to a network share for further third-party scanning
- Files checksum whitelist and blacklist option
- URLs submission for scan and query from emails and files
Monitoring and Report
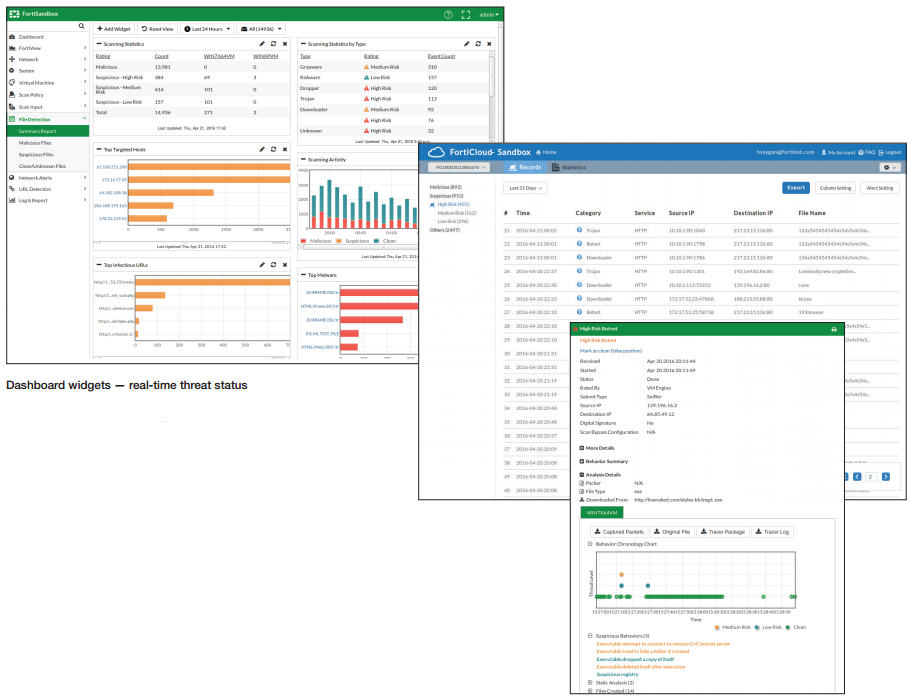
- Real-Time Monitoring Widgets (viewable by source and time period options): Scanning result statistics, scanning activities (over time), top targeted hosts, top malware, top infectious urls, top callback domains
- Drilldown Event Viewer: Dynamic table with content of actions, malware name, rating, type, source, destination, detection time and download path
- Logging — GUI, download RAW log file
- Report generation for malicious files: Detailed reports on file characteristics and behaviors – file modification, process behaviors, registry behaviors, network behaviors, vm snapshot, behavior chronology chart
- Further Analysis: Downloadable files — Sample file, Sandbox tracer logs and PCAP capture
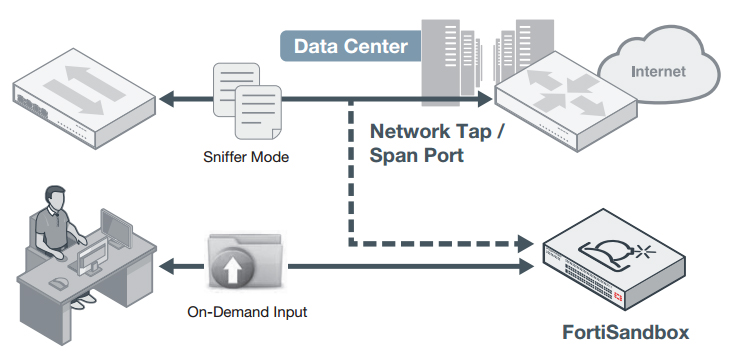
Standalone
This deployment mode relies on inputs from spanned switch ports or network taps. It may also include administrators' on-demand file uploads using the GUI. It is the most suitable infrastructure for adding protection capabilities to existing threat protection systems from various vendors.
Integrated
Various Fortinet products, namely FortiGate, FortiMail, FortiWeb and FortiClient can intercept and submit suspicious content to FortiSandbox when they are configured to interact with FortiSandbox. The integration will also provide timely remediation and reporting capabilities to those devices.
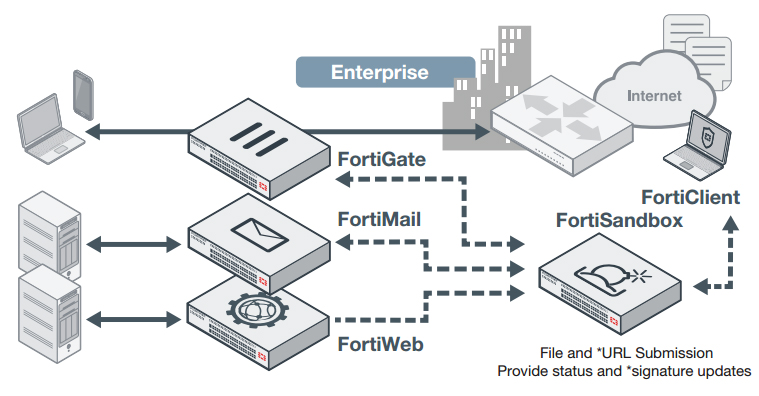
* Not applicable to FortIWeb
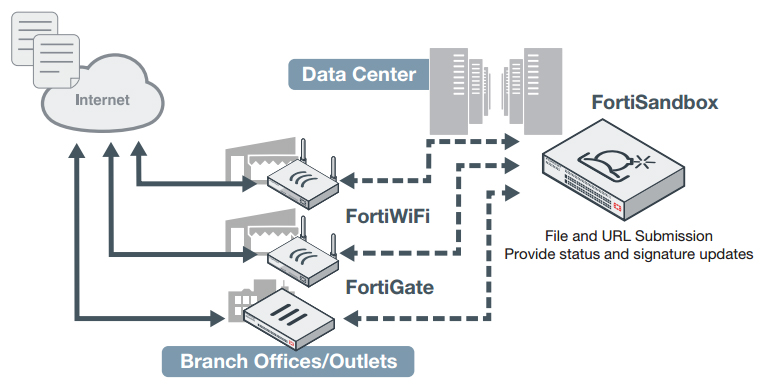
Distributed
This deployment is attractive for organizations that have distributed environments, where FortiGates are deployed in the branch offices and submit suspicious files to a centrallylocated FortiSandbox. This setup yields the benefits of lowest TCO and protects against threats in remote locations.
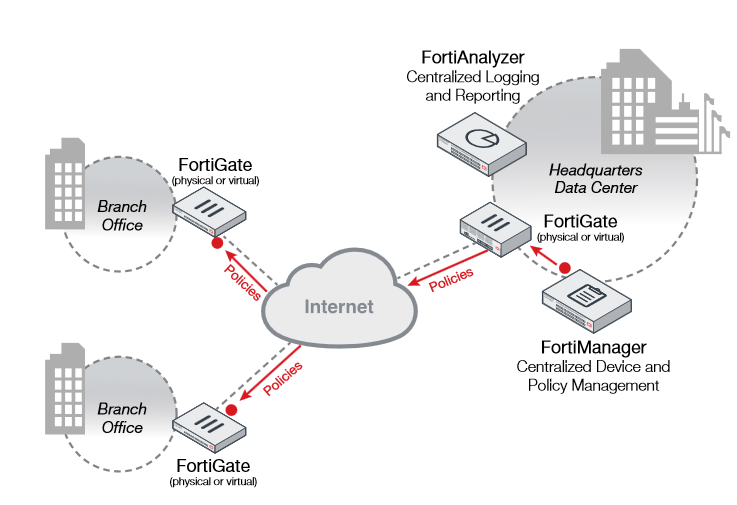
Highlights:
Administrative Domains (ADOMs) and Global Policy
Enables a primary administrator to create groups of devices for other administrators to monitor and manage
- Administrators can manage devices in their geographic location or business division
- Multiple FortiGate virtual domains (VDOMs) can be divided among multiple ADOMs
- Granular permissions allow assigning ADOMs and policies to particular users
- Administrators can only access devices or VDOMs assigned to them
- Create device configuration templates to quickly configure a new Fortinet appliance
- Within each ADOM, there is a common database of objects shared by all devices and policy packages allowing users to reuse similar configurations among a group of managed assets
- Global Policy capabilities are available on all FortiManager hardware models and virtual machines
JSON and XML (Web Services) APIs
- JSON API — Allows MSSPs/large enterprises to create customized, branded web portals for policy and object administration
- XML API — Enables administrators to automate common tasks such as provisioning new FortiGates and configuring existing devices
Locally Hosted Security Content
Hosting security content locally allows the administrator greater control over security content updates and provides improved response time for rating databases. Includes support for:
- Antivirus definition updates
- Intrusion Prevention updates
- Vulnerability and Compliance Management updates
- Web Filtering (select systems)
- Antispam (select systems)
Command and Control
- Manage devices and endpoint agents individually or as logical groups
- Discover new devices automatically
- Create, deploy, and monitor virtual private networks
- Delegate control to other users with distributed administration features
- Audit configuration changes to ensure compliance
Monitor, Analyze and Report
- Access vital security and network statistics
- Real-time monitoring and integrated basic reporting provide visibility into network and user activity.
- For more powerful analytics, combine with a FortiAnalyzer appliance for additional data mining and graphical reporting capabilities
FortiManager Supported Devices
- FortiGate and FortiCarrier Consolidated Security Appliances
- FortiAP Wireless Access Points
- FortiMail Messaging Security Systems
- FortiWeb Web Application Security
- FortiAnalyzer Reporting and Analysis Appliances
- FortiSwitch Switching Platforms
- FortiSandbox Advanced Threat Protection Appliances
